As an Information Security Analyst at Astra, I get to deal with reputed clients from all parts of the world. It is my daily job to test their web applications and do an assessment on every little corner of the website which is something we can’t yet rely on automated scanners to do. However, the excitement of breaking into something new, the faith in the potential that these websites hold for being vulnerable in one or the other bizarre way is something that never disappoints. They always are.
Vulnerability
Let’s call our client FlashyHoldings for the scope of this story. FlashyHoldings is a large online store for clothes and other stuff. Let’s leave it at that. FlashyHoldings is one of our customers who had requested a Security Audit from Astra. Particularly with these E-Commerce websites, the most sought out form of security testing is Business Logic Testing.
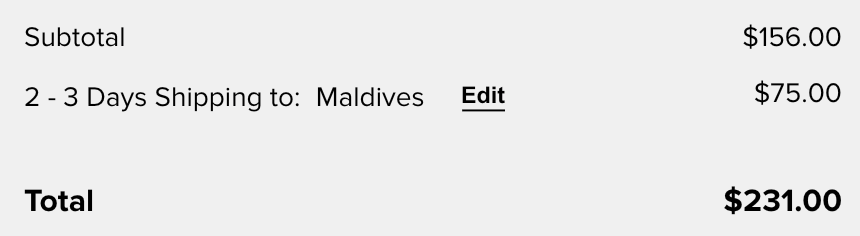
The obvious thing that we security guys working on E-Commerce sites go for is the price manipulation vulnerabilities. Because let’s face it, those are cool! And I did, but to no avail, unfortunately. However just as I was about to wrap up my tests around the checkout page and report on the different vulnerabilities I had found until then, I noticed another POST request parameter holding the 2-letter code for the country I was having a fake order ship to. In this case, the value was MV as I was shipping it to the Maldives, to where the shipping charge is set at $75.
Exploitation
At this point, playing around with the other parameters hadn’t fetched any interesting results in regards to the price manipulation vulnerability that I was going for. I decided to give it one more shot and changed the parameter value to US from MV while making sure that the Shipping Address provided was set to Maldives.
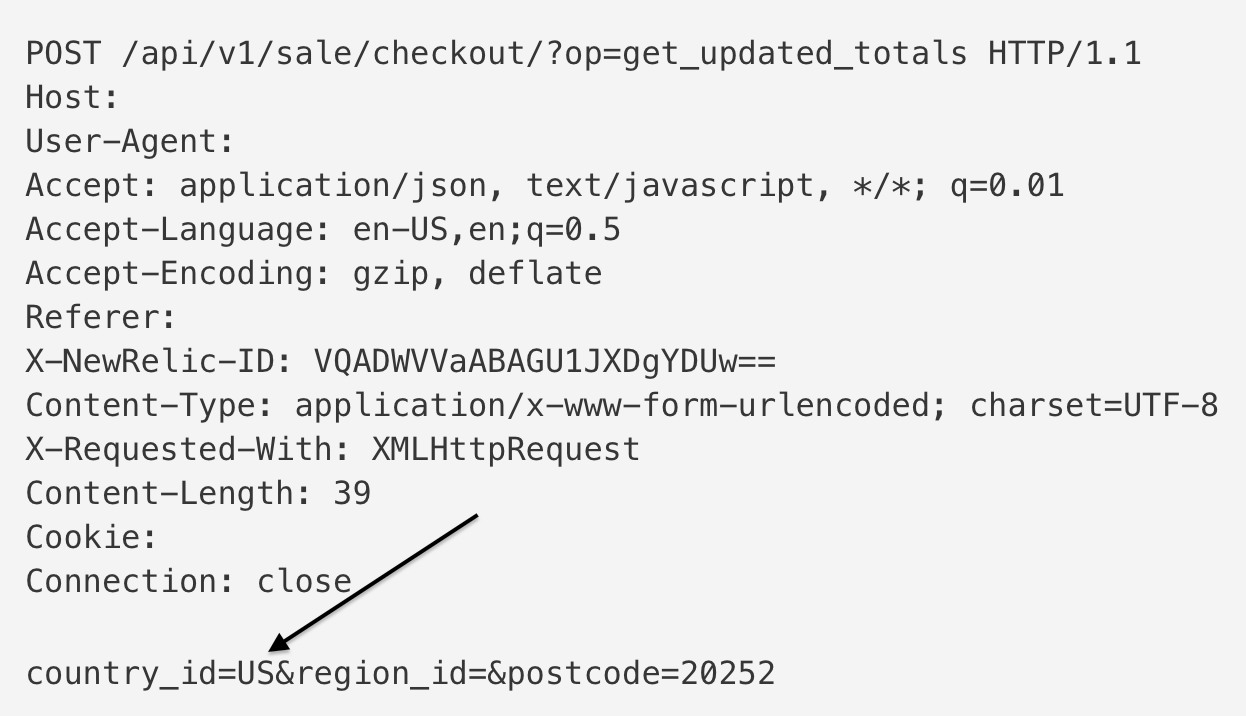
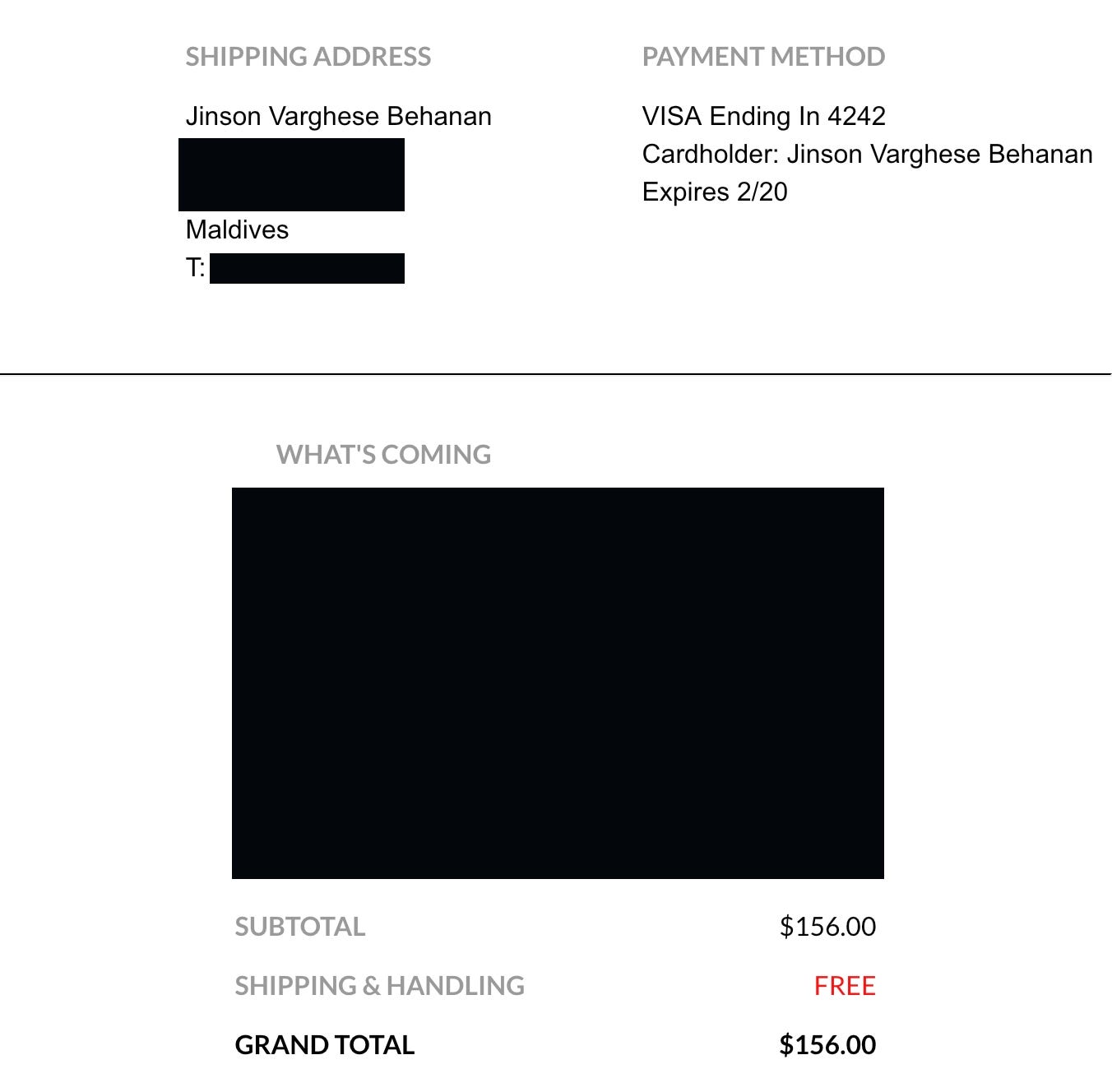
And what do you know?! It worked. My order was finalized and I got the email confirmation that I am being charged absolutely nothing for shipping. And on checking my delivery address, it was indeed getting delivered to Maldives.
PoC Screenshot
Wrap up
After I was done with the testing/audit of the website, we wrapped up the case and reported it. And FlashyHoldings immediately fixed the issues because they knew it better than anyone else the damage that could have been.
While not as remarkable as changing the price of a product to $0.00 and being only one of the different critical vulnerabilities found during my time as a security analyst, this was still interesting and educational to me because FlashyHoldings had done a good job in securing the other parts yet one little detail they overlooked was the one that could have resulted in a loss for them.
Conclusion
Security is not that simple. It doesn’t matter if you are a developer or an ethical hacker, it’s a must to always be thorough. You could easily overlook something that could prove to be costly at a later stage. As seen here, it is indeed possible to manipulate such important details in transactions, in this case, the shipping charge basically changed to zero causing a loss to the business. Therefore it is highly recommended to check your APIs to see if the data is handled server-side or client-side. Additionally, proper data validation checks must be placed for all data sent from the client-side. You can never be too careful.
If you need us to take a look at your web application and perform Business Logic Tests to prevent such exploits, you can always come talk to us at Astra.
I hope you enjoyed the read!
You can follow me on Medium for more stories about the various Security Audits I do and the crazy vulnerabilities I find, as well as on Twitter for more Cybersecurity related news.



